We can’t trust our most precious files and private data with just anyone, especially with the increasingly frequent system breaches and database hacks that have been coming to light recently.
Though there are several options for cloud computing services out there, IAGON provides you with a fully secure solution and ensures you that there is nobody misusing your data, by utilizing 2 layers of security: SHA256 Encryption & Blockchain Technology.
With this structure, we’re encrypting the data files with SHA256 encryption as they come in. Additionally, when storing files on the network, the file is not being stored in one place, at one time, instead, it’s being sharded, meaning it’s being split into several slices and theses slices are then copied several times and spread across the network. So the shard that’s being stored from the miner is not readable because it is not able to be decrypted. In fact, even in the unlikely event that you were able to manage to decrypt a single shard, you won’t be able to read it because you’ll only have one slice of data, and you won’t be locate the others without the private key, that only the owner/user has.

Furthermore, centralized solutions have what is called a Data Lake. The Data Lake architecture is based on implementation of a NoSQL central database, in which files of any sort can be stored and retrieved from, and suggests that once it is hacked, an intruder can “swim” in the databases system, explore the files, and gain access to valuable data describing every aspect of the operations of the compromised organization.
IAGON’s Secure Lake, however, is based on the Blockchain’s unbreakable encryption technology, on file slicing and storage of small, anonymous and strongly encrypted slices of the original files ensures the complete protection of data files, other types of files (such as scans, photos and videos) and databases of any size and ensures the rapid retrieval and update of any stored file. Except from the user who securely uploads a file and has the password (key) to retrieve and encrypt it, no one can read the contents of the small file slices, encrypt, delete, change, retrieve them, identify their source or even associate them with other file slices that are generated from the original, uploaded file.
IAGON’s technology ensures that even when information systems are breached in any way, the data and files that they use cannot be accessed, deleted or otherwise modified.
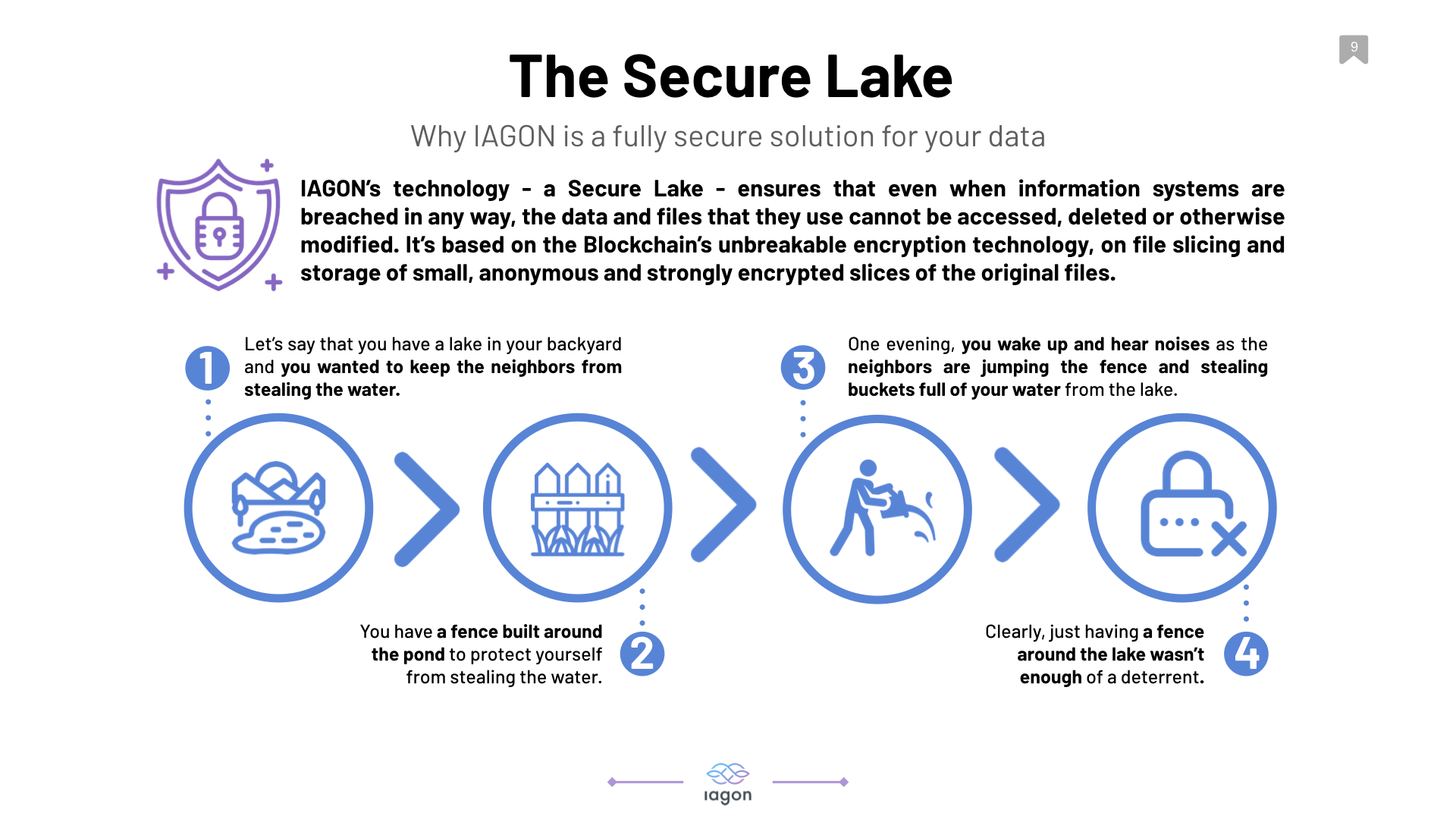
It is important to us that our clients, users, and miners are able to feel 100% secure when utilizing our platform, and these are just a couple of examples as to how we are ensuring that the IAGON platform provides optimal security at all times.
For more information and to see what else is going on @ IAGON, please follow us at the social media links below, or head over to the IAGON Website!

